2500+
Successful Projects

The best practice for responsible mobile app development isn't about racing against the clock to finish your project but about taking a step back and scrutinizing every aspect of the app development process, especially security. With an increasing number of cybercrimes, mobile app security has ascended from being a mere component to a crucial part of the development process.
According to a recent report by Positive Technologies, 43% of Android apps and 38% of iOS apps have been found to have at least one high-risk vulnerability. That’s probably due to the negligence of the security practices in their development. Or worse, they could have abandoned the mobile security testing. Whatever the case, one thing is clear: mobile app security is way more important than you think. Table of Contents
If you’re here to learn more about mobile app security, this guide will greatly serve the purpose. In this blog post, we will discuss some surprising stats related to security breaches, the latest threats and security risks to mobile apps, and the basics of mobile app security and steps to mitigate these threats.
Mobile application security refers to using technology and security measures to defend mobile apps and your digital persona from all types of fraudulent attacks. This includes tampering, malware, key loggers, reverse engineering, and other forms of meddling or disruption. A thorough mobile app security strategy incorporates tech solutions, like shielding, best usage practices, and business procedures.
The significance of mobile app security has surged as mobile devices have become widespread in numerous countries and regions. The growing trend of using mobile devices for banking services, shopping, and other tasks is linked to an increased number of mobile devices, apps, and users. Banks are enhancing their security measures, which is a positive development for those using their mobile devices for banking services.
It is an undeniable truth that no one believes you until or unless they face the same situation, and that’s true in the mobile app development industry. Maybe your app will be the next target for hackers. Mobile app security is indeed essential for businesses, but if you still think you don’t need it right now. Then we won’t give you reasons to opt for mobile app security but actual data of what’s happening right now.
Here are some data-driven stats showing why mobile app security is the need of the hour:
You will be surprised to know that business apps are four times more vulnerable to security threats. Hackers often target these apps to exploit their customers or attack the business itself. Understanding the common threats in mobile app development is essential to stay updated with the latest practices.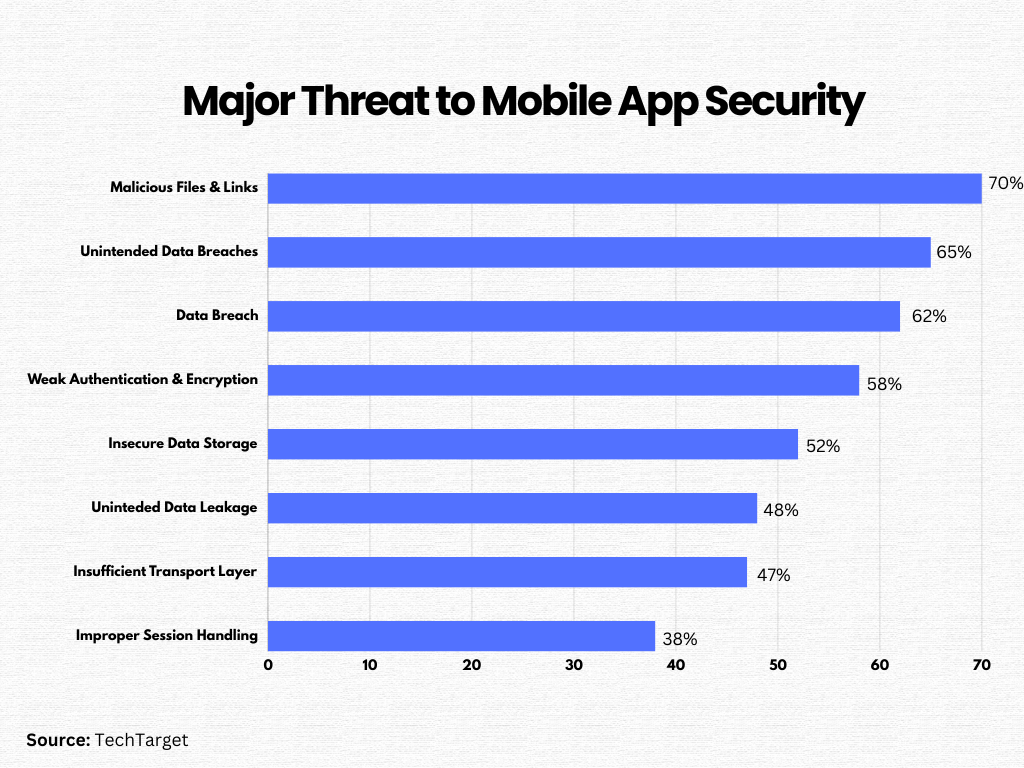
Below, we have listed some of the latest mobile app security threats.
Not only one or two but hundreds of security threats exist in the mobile app landscape. They are not limited to ransomware, trojan horses, worms, and viruses. Each type of threat uses a distinct method to cause harm. They can spread through numerous channels, such as USB devices, social media platforms, compromised websites, downloaded files, and email attachments.
A data breach occurs when unauthorized individuals gain access to confidential information stored on your devices, databases, computer systems, or networks. This event is a significant setback in the mobile app landscape.
During a breach, sensitive data, including personal, financial, and proprietary information, can be unlawfully modified, stolen, or exposed. Data breaches can occur in various ways, including physical theft, attacks from within the organization, and external attacks.
Inadequate authentication is a significant issue in digital systems, particularly in mobile apps. Users requiring access to confidential data or services must authenticate themselves before their requests can be processed. However, if the authentication processes are poorly designed or implemented, it can lead to disastrous outcomes.
In such situations, unauthorized individuals can exploit weak authentication processes to gain unauthorized access, posing a severe threat to both individual users and businesses. Factors contributing to these mobile app risks include poor password practices, absence of Multi-Factor Authentication (MFA), and inadequate session management.
Encryption is a crucial security measure that safeguards sensitive information from hackers. However, data breaches can occur due to hasty deployment, poor implementation, or incorrect selection of encryption policies.
When a mobile app or any digital system doesn't have robust cryptographic measures, it's referred to as "poor encryption." Attackers can exploit this weak encryption in various ways, including cryptanalysis, brute-forcing, dictionary attacks, eavesdropping, replay attacks, key management, side-channel attacks, Man-in-the-Middle, padding oracle, and key length reduction.
Harmful mobile code can alter the application without the user's consent, causing disruptions to the application's operation or the device itself. It includes viruses, trojan horses, worms, script-based attacks, backdoors, and more.
Recently, these threats have evolved into more sophisticated forms using mobile-related technologies like HTML, VBScript, JavaScript, Java applets, ActiveX, etc. While mobile malware isn't as prevalent as spyware targeting traditional workstations, it's an emerging threat to consumer devices. As attacks become more frequent and potent, mobile malware presents a significant challenge to the mobile security industry.
In the client-server model of mobile app security, data is transferred across carrier networks and the Internet. Attackers can exploit vulnerabilities in this data exchange to launch malware attacks and even intercept private data stored across local networks or WiFi.
These vulnerabilities expose end users to risks such as phishing, man-in-the-middle attacks, site disclosure, and account theft.
Unlawful mobile device unlocking practices, often referred to as "jailbreaking" for iOS devices and "rooting" for Android devices, allow users to gain complete control over their device's operating system and all its applications.
However, this process opens up a pathway for malicious actors to carry out harmful activities such as stealing data, spreading malware, escalating privileges, creating botnets, logging keystrokes, installing insecure apps, and evading security measures.
Data that is not encrypted or poorly encrypted while in transit poses a significant risk. Attackers can easily intercept this data as it travels over Wi-Fi networks, particularly unsecured public Wi-Fi or a mobile device's carrier network.
Even though data in transit is typically encrypted, it can often be misconfigured, or the encryption keys can be poorly managed. Implementing robust encryption standards can help mitigate these risks.
If your mobile app asks excessive permissions than necessary, it can be a threat to your device security. These excessive permissions make it easier for malicious actors to carry out harmful activities and breach sensitive data.
It's advisable only to grant permissions that are essential for the app's operations. In other words, if permission doesn't seem necessary for the app to function properly, it's best not to grant it.
While mobile apps are designed to protect your data, inadequate security measures can lead to data leaks. A successful data breach allows attackers to gain unauthorized access to sensitive data stored in your app's database.
Data leakage occurs when sensitive information is transferred without proper authorization due to insufficient security measures within mobile applications.

To mitigate the growing security threats to mobile apps, here’s a list of some best practices you should follow in 2025:
Authentication is a crucial step in app development to enhance the security of mobile applications. It confirms the user's identity using various methods, such as user ID, password, fingerprint, or one-time passwords. Granting access to authenticated users can deter hackers, thereby preventing data breaches and other harmful activities. Certain apps, especially those handling sensitive user information like banking details, require two-factor authentication. This additional security layer fortifies mobile applications against potential threats.
Another mobile app security mechanism is Encryption, which ensures the security of mobile app data during storage and transfer. Two primary encryption methods are widely used: symmetric and asymmetric. Symmetric encryption utilizes a single key for data encryption and decryption, while asymmetric encryption employs two distinct keys for these processes.
Consumer concerns over cybercrimes continue to drive changes in data regulations and privacy laws. Yet, many mobile app development companies overlook the criticality of secure data storage.
When designing data storage systems, it's essential to refrain from sharing sensitive information with third parties, keyboard caches, IPC mechanisms, app logs, and user devices.
Local storage of your app's data and code should be avoided. Instead, employ encrypted containers for data storage. Additionally, incorporate an auto-delete function in your data storage systems to erase data automatically after a specified duration.
Also, ensure the encryption of user credentials and files using KeyStore, keychain, and SQL server. Conduct comprehensive analyses through data analytics.
Before launching your mobile app, ensuring its functionality and user-friendliness is crucial. A comprehensive security audit is also necessary to identify any potential weak points in your application. This security maintenance should continue even post-launch.
Here are some steps you can take to conduct a thorough security penetration testing:
Regular testing is required to identify potential threats. For in-depth penetration testing, consider hiring a network security specialist.
There are several data protection laws for mobile app development companies. These include the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA) and other local regulators.
Here are some key strategies for maintaining compliance with these data protection laws:
APIs serve as the connectors between various software elements, and their protection is vital to avoid possible data leaks. By securing endpoints, implementing rate limits, and conducting frequent audits, we can ensure these connectors are resistant to threats.
Coding forms the foundation of any application, and its security is of the utmost importance. By adopting secure coding practices, developers can fend off a variety of attacks, from SQL injections to cross-site scripting, ensuring the core of the app remains invincible.
Setting up a robust development environment is the first step toward mobile app development. Keeping your tools, libraries, and access controls current and secure can reduce vulnerabilities from the start of the app's creation.
Use access controls to restrict what each user can view or do within your app. As one of the best practices for mobile app security, this method can stop unauthorized users from accessing confidential information.
For instance, you can utilize role-based access control (RBAC), which enables you to assign permissions based on roles within your organization.
Consider inviting external experts to uncover vulnerabilities in your mobile app. This can be an effective method of detecting and addressing potential security weaknesses.
For instance, Initiate a bug bounty program where cybersecurity experts are incentivized to identify and report security flaws. This promotes a proactive strategy to identify and rectify security vulnerabilities before malicious entities can exploit them.
Despite all precautions, security breaches can still happen. A solid response strategy ensures prompt action, reduces damage, and guarantees a speedy recovery while advising users on subsequent steps to protect their data.
By following these recommended practices, developers and businesses can maintain a strong defense against potential cyber threats, ensuring a secure environment for their operations and their users.
The increasing adoption of mobile applications is paralleled by a rise in cyber threats, making mobile app security a significant issue. It's crucial for business owners to be vigilant about potential threats to ensure their applications remain secure.
Implementing best practices for mobile app security during the development process can help create secure apps for both Android and iOS platforms. Our team of expert mobile app developers at Mtoag Technologies has created this guide based on their expertise, experience, and industry knowledge. We have a track record of consistently developing and delivering secure mobile applications tailored to the unique needs of various businesses.
If you're in search of a reliable mobile application development company to help expand your business, we're here to help. Get in touch with us to learn more about our mobile application development services.