2500+
Successful Projects
With an increasing focus on Cloud and Software-as-a-Service (SaaS) services, SAML has emerged as a hot topic among industry insiders in terms of authentication. We know how crucial federated identity is for users to have secure web access in this technology-driven environment. And without robust federated identity standardization mechanisms, it is nearly impossible to expand single sign-on (SSO) across multiple applications in an economical way.
Table of Contents
In such a situation, Secure Assertion Mark-up Language (SAML) has emerged as a leading federation standard, thanks to its established security, verified interoperability, and global deployments involving thousands of web applications.
While most tech-savvies like us understand the role of SAML in web development, many are even unaware of what it actually is, especially businesses from non-technical backgrounds. So, if you’re among them, let this blog be your guide to understanding what SAML is, how it works, and why it’s crucial for web development. 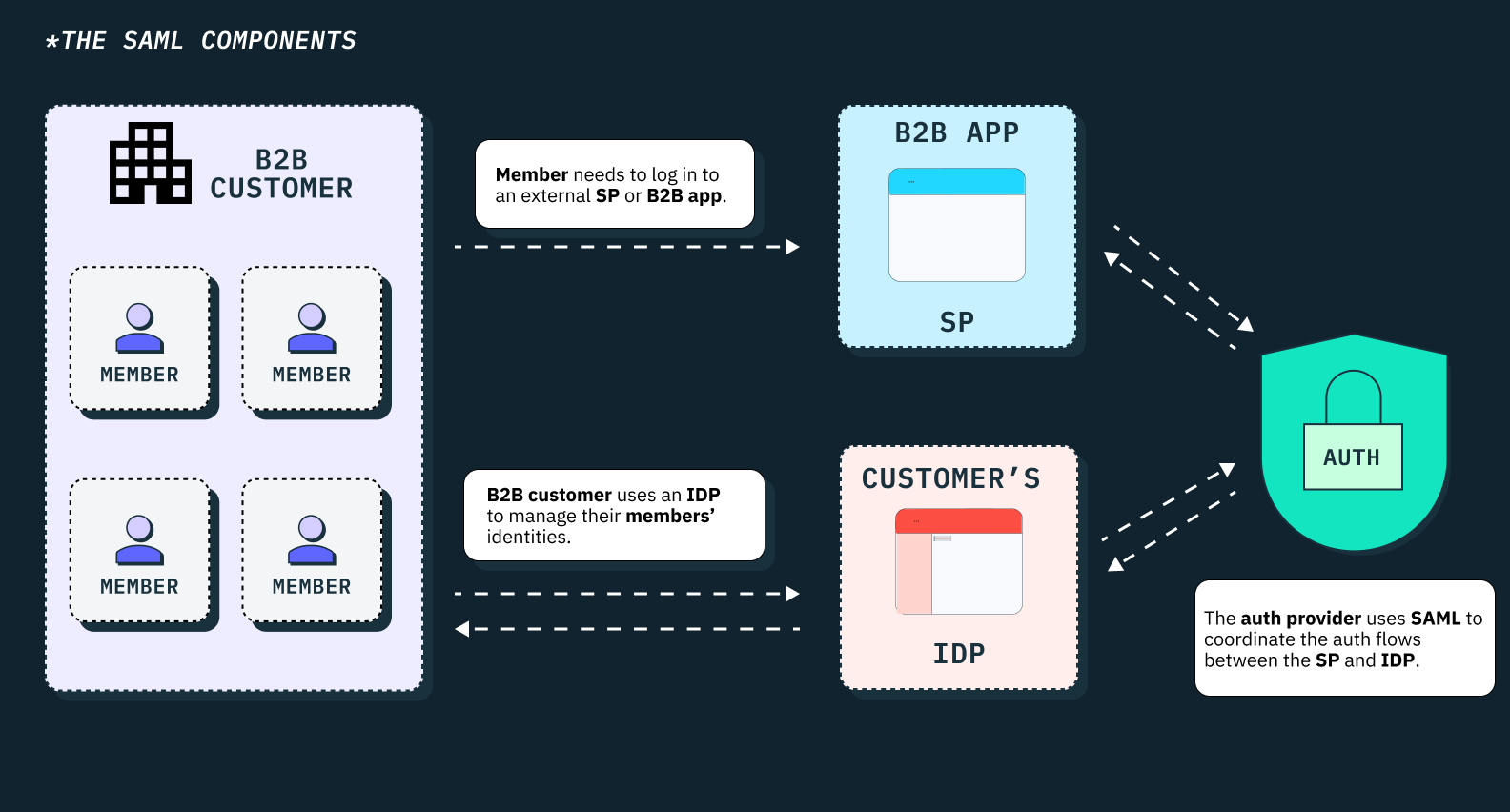
SAML is an acronym for the Security Assertion Markup Language, an open federation standard that connects an identity provider (IdP) with a service provider (SP).
The SAML IdP verifies the users and sends them an authentication token that the SP can use. SAML makes the SP’s job easier, as it does not need to authenticate the users themselves and can use the identity to work with both internal and external users.
It also lets the SP access security credentials from the IdP over a network, usually an application or service. SAML allows safe and seamless communication between the public cloud and other systems that use SAML, as well as some other identity management systems that are in the same or different cloud.
With SAML, businesses can give their users a single sign-on (SSO) experience across any two applications that support SAML protocol and services. The SAML SSO can handle various security tasks for one or more applications.
OASIS is a group that oversees and updates this protocol through its SSTC branch. OASIS has launched three SAML versions so far: SAML 1.0, SAML 1.1, and SAML 2.0. The newest version (SAML 2.0) is based on the previous SAML 1.1 version, but it has some changes that make it incompatible with the older versions.
SAML 2.0 is the latest version of SAML. This means that SAML 2.0 does the same thing as SAML 1.1: It lets users access various services with the same identity credentials that they use for other services, such as Facebook and Google.
SAML is often compared to LDAP, which is another way of managing user identities and access. When a user wants to use an online service with SAML authentication, they do not need to enter their username and password again for that service. Instead, the SSO SAML service sends them to a page where another system's credentials—like Google's—confirm who they are.
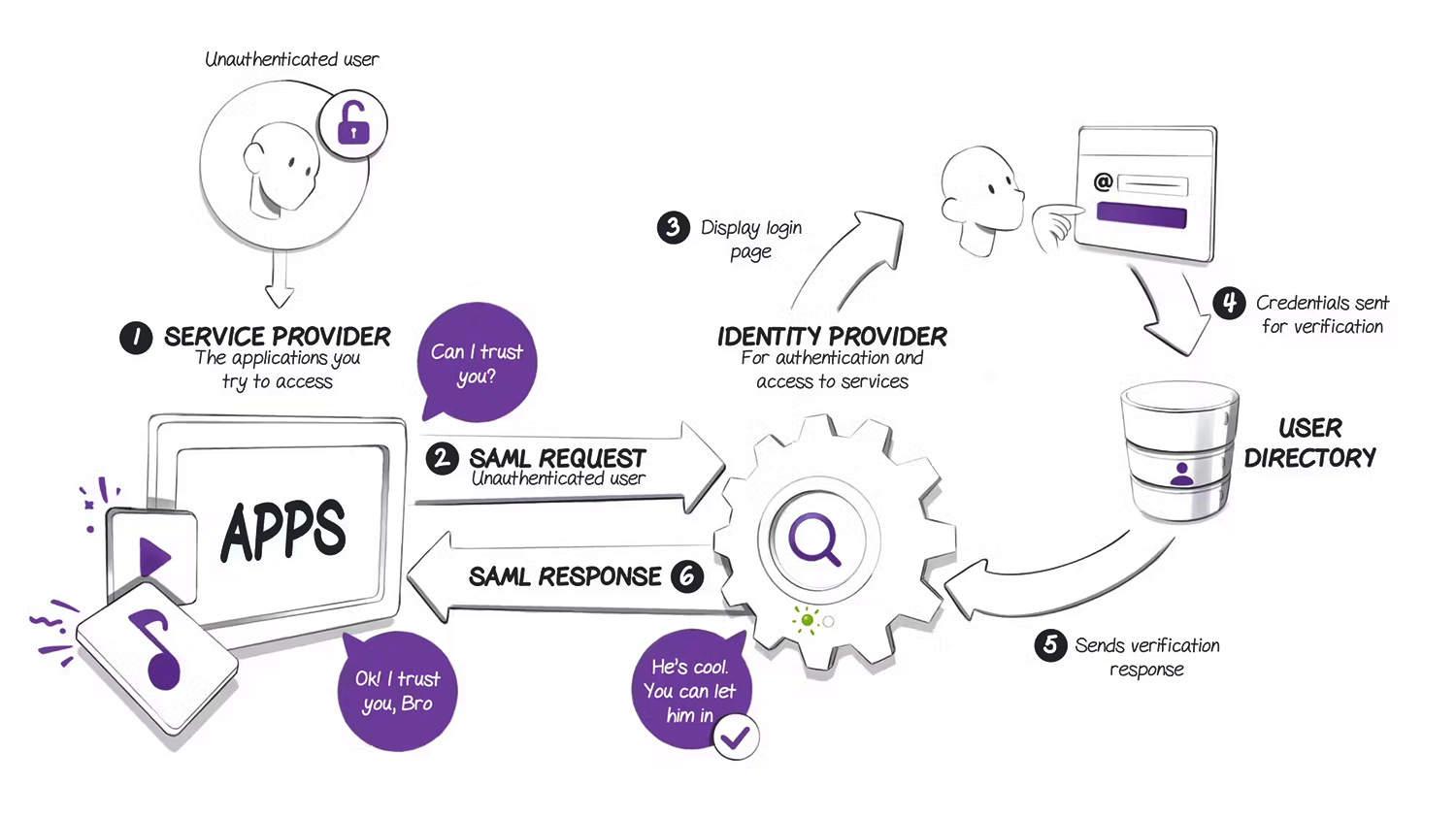
To understand the topic more precisely, we have listed down some common SAML terms.
This is the online app or service that users want to access. Some common examples are cloud email services like Gmail and Microsoft Office 365, cloud storage services like Google Drive and AWS S3, and chat apps like Slack and Skype.
Normally, you would sign in to these services directly, but when you use SSO, you sign in to the SSO instead, and SAML is used to grant you access instead of a direct login.
An Identity Provider (IdP) is the entity that gives you an identity, including the ability to verify who you are. The Identity Provider also has your user profile: extra information about you such as your name, job title, phone number, address, and so on.
Depending on the app, some service providers may need a very simple profile (username, email), while others may need more user data (job title, department, address, location, manager, and so on).
A SAML Request, also called an authentication request, is created by the Service Provider to "ask" for an authentication.
A SAML Response is created by the Identity Provider. It has the actual statement of the authenticated user. Also, a SAML Response may have more information, such as user profile information and group/role information, depending on what the Service Provider can handle.
Identity federation is the process of giving authentication responsibility to trusted identity providers. SAML and similar technologies, like OAuth and Web Services Federation (WS-Fed), use identity federation to securely re-use existing credentials in multiple apps.
SAML assertions are the messages an identity provider sends to a service provider that has authentication, attribute, or authorization decision information.
For example, a SAML assertion can give either a Yes (authenticated) or No (authentication failed) response to a service provider.
SSO is a way to sign in to multiple apps while entering login details only once. With Duo SSO, for example, users can sign in to a single, MFA-protected dashboard to get access to all of their apps, both cloud-based and native.
SAML tokens are XML-formatted documents that have the claims or SAML assertions that one entity makes about another. For example, an identity provider can say or assert that a user is really who they claim to be. The SAML token is verified by the service provider because it has a digital signature from the security token service.
SAML Certificates are digital certificates that make authentication more secure for applications that use the SAML authentication protocol. SAML signing and encryption means that public keys, or certificates, are used to check the data that is sent between the Service Provider (SP) and Identity Provider (IdP).
SAML certificates are different from SSL (TLS) certificates, which are used for the application’s browser and are set up and maintained by the server.
LDAP is an open standard used to get directory information over an IP network. While SAML and LDAP are both authentication protocols, they work differently and are used for different purposes.
For example, LDAP is often used for on-site authentication, while SAML takes user credentials to cloud apps.
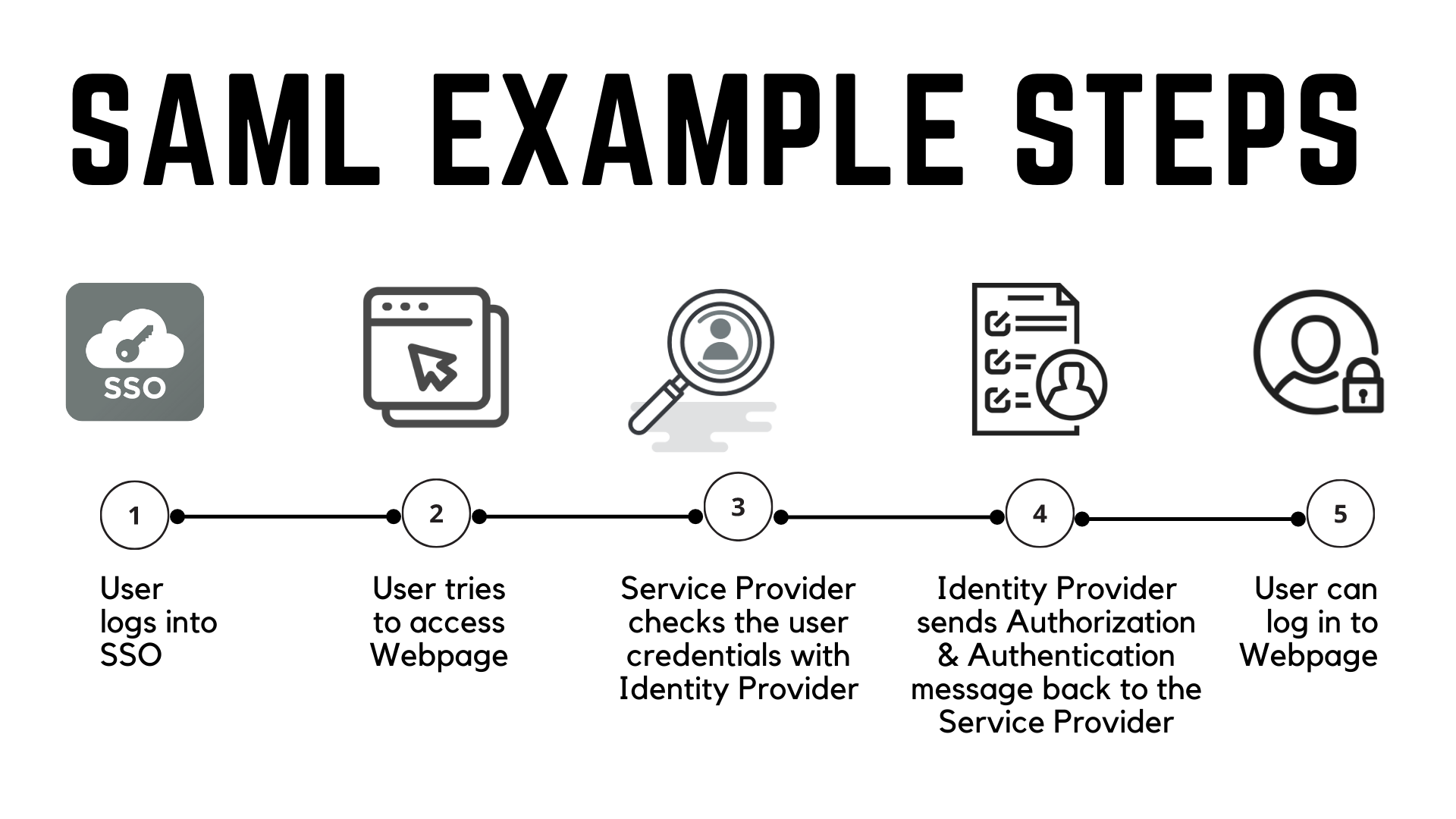
SAML works by sharing information about users, logins, and attributes across different systems. The identity provider is the system that verifies the user’s identity and asks for two-factor authentication, such as Duo Access Gateway.
The user only needs to log in once with the identity provider, and then the identity provider can send SAML attributes to the service provider when the user tries to access it.
The service provider asks the identity provider for the authorization and authentication. Both systems use the same language - SAML - so the user does not need to log in again.
SAML uses some key technologies that are hidden from the user, such as
SAML consists of different entities and components that make it one of the most secure federated identity standardization mechanisms. So, let’s take a look at some SAML components and entities.
SAML is categorized into three broad categories in terms of entities:
SAML has four main types of components: Assertions, Protocols, Bindings, and Profiles. Let’s understand these SAML components in brief.
A SAML assertion is a piece of information that contains zero or more statements issued by a SAML authority, a system that produces SAML authentication assertions. SAML identity providers are examples of such systems.
SAML defines three kinds of assertions -
SAML establishes its own general protocols for request/response interactions between systems and the entities that can be verified – either principals or subjects. SAML 2.0 protocols include the following:
SAML relies on several other protocols that are used to format and exchange SAML requests and responses. These include the following:
SAML bindings show how SAML protocol messages are sent. They leverage the transport protocols to communicate between SAML entities. SAML 2.0 defines the following bindings:
SAML profiles are combinations of SAML assertions, protocols, and bindings. SAML profiles are used to create specific applications. The following profiles are defined for SAML 2.0:
These profiles can be set up to enable an SSO deployment.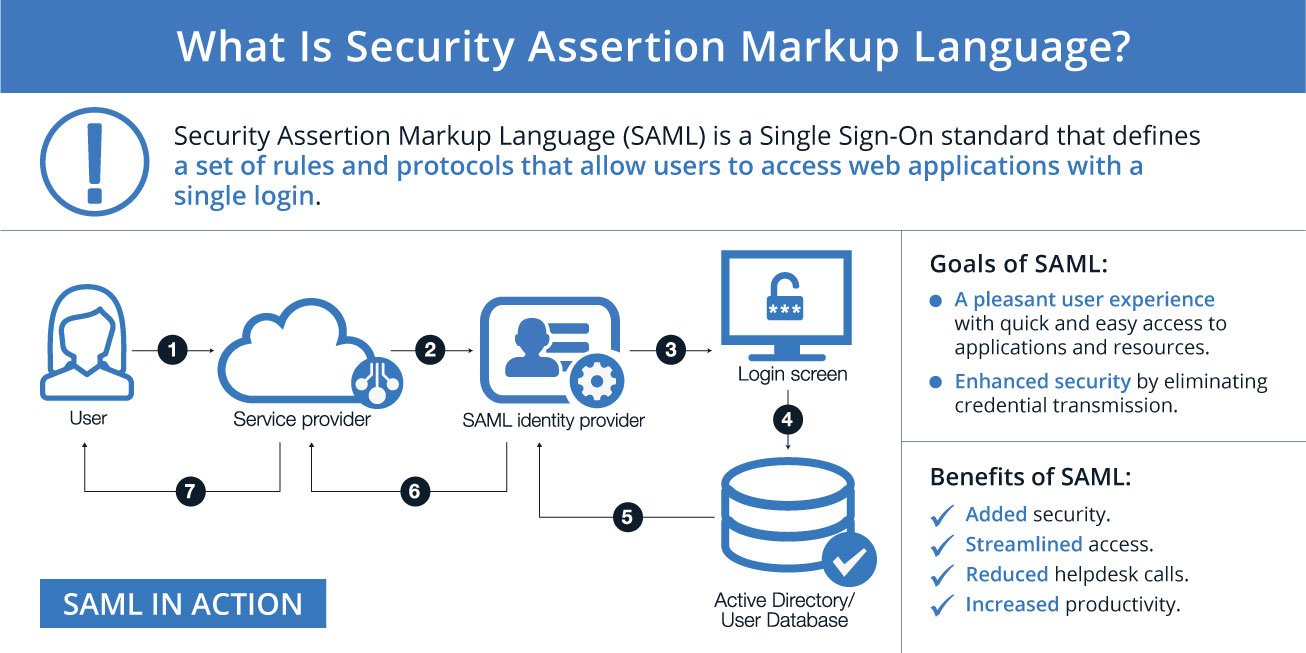
SAML is mainly used to allow web browser single sign-on (SSO). The user experience goal for SSO is to enable a user to log in once and access different systems that are separately secured without entering credentials again. The security goal is to make sure the authentication standards are satisfied at each security boundary.
Some advantages of SAML include
SAML authentication is the process of verifying a user’s identity and granting access to a service based on the user’s attributes. SAML authentication works by sending a SAML request from the SP to the IdP, which then validates the user’s credentials and returns a SAML response containing the user’s attributes and a digital signature. The SP verifies the signature and grants access to the user based on the attributes.
SAML single sign-on (SSO) is a feature of SAML authentication that allows a user to log in once and access multiple services without re-entering credentials. SSO improves the user experience and security by reducing the need for multiple passwords and login screens.
SSO also simplifies the management of user accounts and permissions across different services. SSO works by using a SAML assertion, which is a piece of XML data that contains the user’s identity and attributes, as a token to access the services. The SAML assertion is issued by the IdP and consumed by the SPs.
OAuth and SAML are both methods we use for granting access. However, the main distinction between the two is that we use SAML for verifying who the user is (authentication) and OAuth for specifying what the user can do (authorization).
Here’s a Side-by-side Comparison between OAuth and SAML:
Point of Differences | OAuth | SAML |
Purpose | OAuth is an authorization protocol that allows a user to share access to their resources with a service provider. | SAML is an authentication protocol that allows a service provider to verify the identity and attributes of a user. |
Proof | Uses access tokens as proof of authorization | Uses SAML assertions as proof of authentication |
Use Case | More suited for delegation of authorization to third-party applications, such as social media or cloud services. | More suited for federation of authentication across secure domains, such as enterprise or government applications. |
Web Service | Based on RESTful web services | Based on SOAP web services. |
Compatibility | Compatible with OpenID Connect | Compatible with WS-Federation |
The role of SAML in web development is undeniable. With it, website developers can easily integrate their applications with different identity providers. This means they don’t have to manage user accounts and passwords themselves, which reduces the risk of security breaches and simplifies user management.
SAML also improves the user experience, as users don’t have to remember multiple passwords or fill in login forms repeatedly. SAML is an open standard that works across different platforms and languages, making it a versatile and reliable solution for web development companies.
Overall, SAML is a powerful and widely adopted federated identity standardization mechanism that enables single sign-on across multiple applications and services.
By using SAML, users can enjoy a seamless and secure authentication experience, while service providers can reduce the complexity and cost of managing user accounts and passwords.
All in all, SAML turns out to be an essential component of modern web development, as it simplifies and strengthens the authentication process for both users and service providers.
An assertion is a statement about a user's identity and attributes that is digitally signed by an identity provider.
Idp stands for identity provider, a service that authenticates users and issues assertions.
SAML stands for Security Assertion Markup Language, a standard protocol for federated identity and single sign-on.
An Idp SAML is an identity provider that supports the SAML protocol and can communicate with SAML service providers.
SAML is used for enabling single sign-on across multiple applications and services, as well as exchanging user information and authorization data.
A SAML login page is a web page that redirects users to their Idp for authentication and then sends them back to the service provider with an assertion.
No, SAML can also be used for other purposes, such as attribute exchange, identity federation, and authorization decisions.
OAuth and SAML are different protocols that serve different use cases. OAuth is mainly for delegating access to resources, while SAML is mainly for authenticating users and exchanging identity information.