2500+
Successful Projects

The global mobile app security landscape has witnessed drastic changes and transformations in the last few years due to digitalization and regulatory adjustments. With cyber-attacks continuing to be the biggest nightmare for developers and businesses alike, mobile app development companies have now started placing a paramount focus on the app’s security by integrating the necessary measures throughout the mobile app development lifecycle. It majorly includes ensuring compliance with the Personal Data Protection Laws.
According to the latest State of Application Strategy report, 48% of Indian mobile app development companies have already adopted a Secure Development Life Cycle (SDLC) approach to security. The integration of security practices in the early stages of development can help the development team identify and fix vulnerabilities quickly.
Table of Contents
You might be wondering how mobile app security has become a big issue. Well! It is probably due to the increased cyber attacks around the world. Did you know that one in every four mobile apps on app stores has at least one high-risk security flaw? But that’s not the only reason; there are many more you will discover when you start reading this blog.
This guide to mobile app security will help you understand its significance, common security threats, and best practices for mitigating them. So, let’s get started!
Mobile application security refers to using technology and following strict security measures to defend mobile apps and user’s personal data against all types of fraudulent attacks. This includes tampering, malware, key loggers, reverse engineering, and other forms of meddling or disruption.
A thorough mobile app security strategy incorporates tech solutions, like shielding, best usage practices, and business procedures. The significance of mobile app security has increased with the wide adoption of smartphones.
The most common mobile app security threats include
In a world where cyber attacks have become a common phenomenon, with an average of 97 internet users falling victim to cyber crimes every hour, your app could potentially be the next on a hacker's hit list.
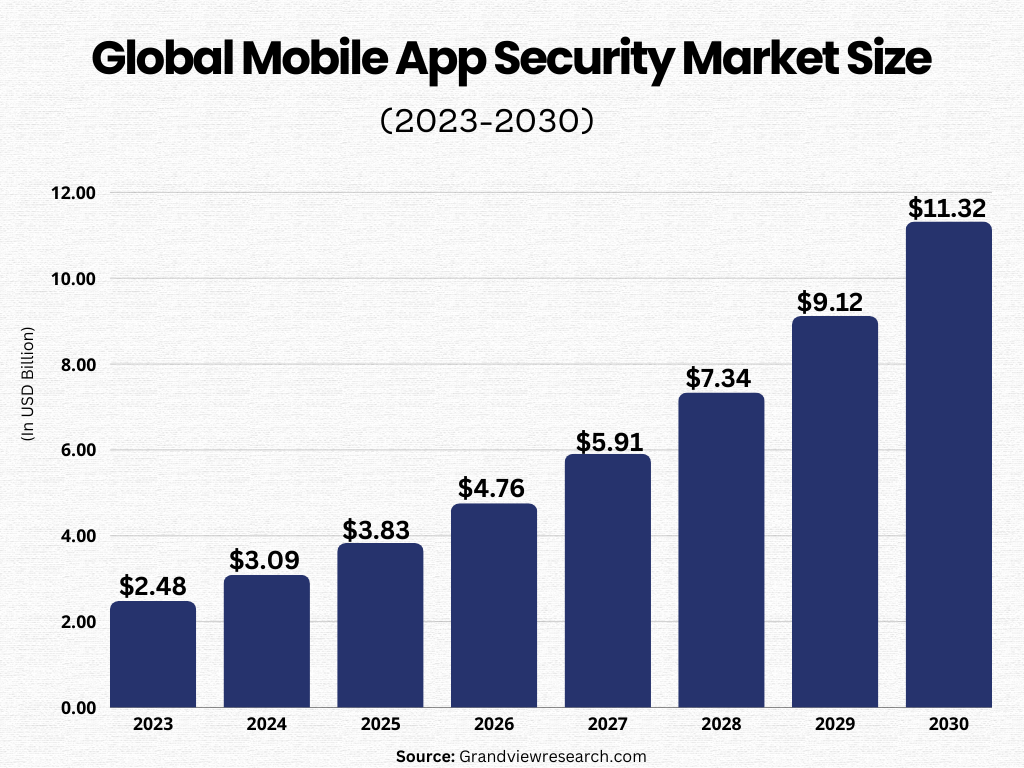
While the importance of mobile app security for businesses is undeniable, if you still believe it's not a pressing need, we won't try to convince you with reasons. Instead, we'll present you with real-time data reflecting the current situation.
Here are some statistics that underscore the critical need for mobile app security in today's digital age:
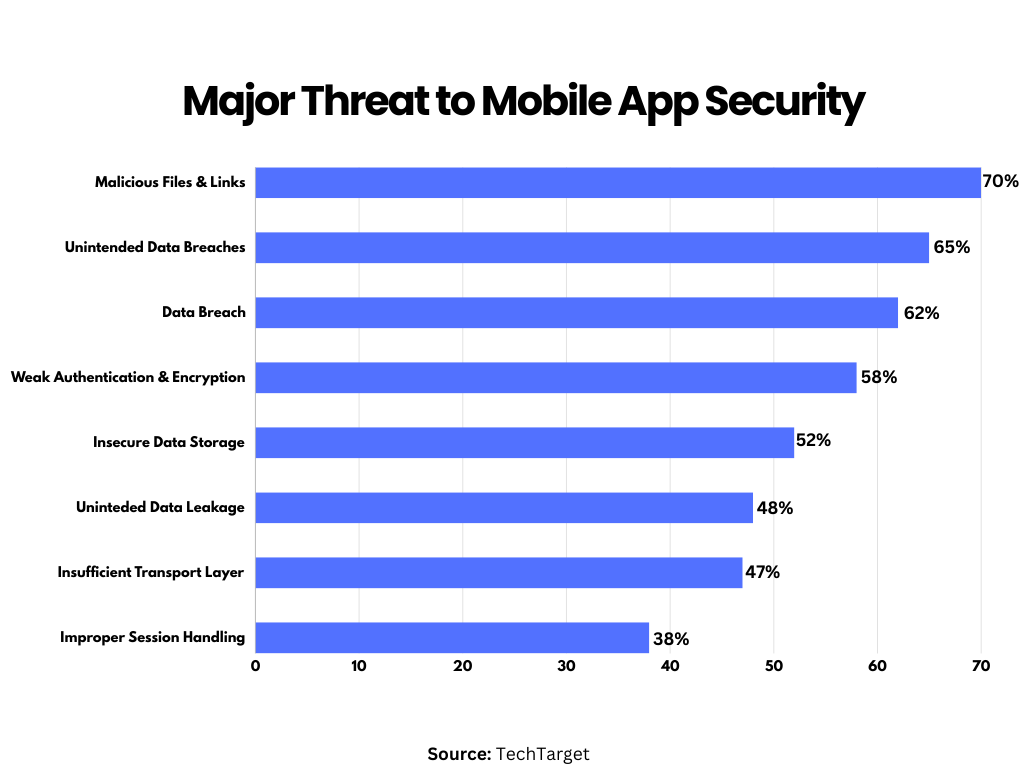
With digitalization reading like wildfire, there has been an increase in mobile app security threats that can negatively impact the app’s user interactions and the overall mobile ecosystem.
Understanding these security vulnerabilities will help you prepare in advance and give you time to develop and implement a strategic security measure.
Here are some common security threats to mobile apps:
Mobile devices are constantly threatened by malware and harmful apps. These applications are engineered to exploit weak spots, illicitly access confidential data, or interfere with device operations.
Mobile apps that handle sensitive user data can potentially leak this information. This could be due to inadequate data management, a lack of encryption, or unsecured communication channels.
Hackers often try to access user accounts by exploiting weak authentication systems or using stolen login details. This is the most common security threat in mobile apps, with more than 82% of security breaches being caused by authentication issues in 2023.
In these attacks, hackers intercept communication between an application and its backend servers or between two users, enabling them to listen in, alter, or insert harmful content into the conversation.

This involves tricking users into compromising their own security, such as coaxing them into divulging confidential information, clicking on harmful links, or downloading infected applications.
Jailbreaking (for iOS) or rooting (for Android) devices can bypass security protocols and give hackers deeper access to the operating system, potentially jeopardizing application security.
Hackers may insert harmful code into an application to exploit weak spots or illicitly access data or system resources. To avoid this, you should prioritize code security in your SLDC.
Inadequate or vulnerable data storage practices can expose sensitive information to unauthorized access. These practices include storing data in unencrypted form, using weak encryption methods, or storing data in easily accessible locations.
To deduce sensitive data, these attacks exploit information leaked during an application's operation, such as timing variations, power usage, or electromagnetic emissions.
Phishing remains one of the most significant security threats in which hackers try to trick users into revealing their login details or sensitive information by imitating legitimate application interfaces or sending misleading messages.
Security weaknesses can be introduced into mobile applications through vulnerabilities in third-party libraries, software development kits (SDKs), or application programming interfaces (APIs). Moreover, neglecting mobile application security standards during custom mobile application development is a common reason for intruders to exploit them for unauthorized access or data breaches.
If a device is stolen or lost, unauthorized persons may gain physical access to the application and its data. This can result in data breaches and unauthorized use without sufficient security measures.
To counter these threats, mobile application developers must employ a robust mobile application security checklist, including secure authentication mechanisms, encryption, and regular security assessments. Continuous monitoring and updating security protocols are vital to tackling emerging mobile app security threats and vulnerabilities.
Developing a secure mobile app requires the development team to follow the security best practices. As said, integrating the security measures in the early stages of the mobile app development lifecycle will help developers identify and fix security flaws quickly.

To help you keep your mobile app secure and safe from security threats, here are the latest best practices you should follow in 2024:
Securing your codebase is probably the first step towards implementing mobile app security. This can be achieved through code encryption, which acts as a barrier against hackers who may attempt to access, alter, or exploit your code. This could potentially prevent reverse engineering attacks or the exploitation of security vulnerabilities.
Studies have revealed that 82% of security flaws in mobile apps are found within the source code. Encrypting your code can deter attackers and avert harmful security breaches. As a developer, it's also advisable to sign your code during the development of mobile applications.
Alongside code encryption, it's crucial to verify your code’s authentication using a code-signing certificate. This enables you to digitally endorse your code with a private key while also making a public key available for user inspection.
A code-signing certificate serves as an assurance that your mobile application is authentic, originates from a reliable source, and remains unaltered. Since malware can be disseminated by mimicking legitimate sources, this certificate gives users confidence in a mobile app's legitimacy.
However, bear in mind that code-signing certificates have a validity period of one to three years, necessitating regular renewal.
Mobile apps often store unstructured data either in a local file system or a device storage database. In the absence of encryption, attackers can access this data, posing a significant security threat. Encrypting this data can mitigate this risk.
To keep sensitive information out of the reach of attackers, consider implementing data encryption in your mobile app using SQLite Database Encryption Modules or file-level encryption across various platforms.
Regardless of the method you opt for, ensure all sensitive data is encrypted prior to storage on your server or in your database. Additionally, always employ the most recent cryptographic techniques and conduct penetration testing on your mobile app prior to launch to guarantee robust security.
To protect your mobile app against potential threats, it's crucial to implement the latest and updated security algorithms. Attackers often target outdated encryption versions, so employing the newest algorithmic version enhances your app's security.
The Advanced Encryption Standard (AES) is a widely used encryption algorithm. AES operates on a symmetric key principle, meaning the same key is used for both data encryption and decryption. You can choose from various AES encryption versions, such as 512-bit, 256-bit, and SHA-256 hashing.
Testing your code for security vulnerabilities is vital in safeguarding your mobile app and maintaining alignment with security standards. If attackers manage to access sensitive customer information or proprietary company data within your app, it could result in severe security breaches.
Regular and thorough penetration tests can help detect and fix these security glitches before they cause significant damage to your app and its compliance certifications.
To ensure effectiveness and reduce your workload, consider delegating this crucial testing to experts like NowSecure, renowned for their successful and repeatable penetration testing.
When data is transmitted from a mobile device to server-side endpoints, attackers may intercept HTTP communication. Several methods, including Transport Layer Security (TLS) and Certificate Pinning, can be used to secure data during transit.
TLS, an evolution of Secure Socket Layers (SSL), allows you to encrypt data in transit using public key cryptography. While TLS doesn't secure data on end systems, it prevents data access during digital transit. Certificate Pinning cross-verifies whether a digital certificate matches the claimed domain name using a set of public keys.
When deciding on a method to secure your data in transit, consider your mobile app's requirements, the sensitivity of your data, and potential security risks.
If your mobile app development involves third-party services, ensure you use only authorized APIs. Unauthorized third-party APIs could inadvertently provide an attacker with privileges, jeopardizing your data.
The use of unauthorized APIs could also lead to your app being rejected and removed from app stores. Therefore, adhere to the specific platform guidelines for authorized APIs to ensure maximum security and compliance.
When your mobile app is being used by numerous users, it's crucial to have a reliable authentication system in place. This could involve updating robust alphanumeric passwords every quarter, employing multi-factor authentication, or even using biometric authentication.
Although biometrics tend to be more secure than passwords, they can be costlier and more challenging to set up. Regardless of your authentication method, it's important to periodically reassess your strategies and adjust them as necessary to maintain your app's security.
Given that your app's sensitive data is stored in the backend, it's vital to prevent this data from being accessed by unauthorized individuals. One way to do this is by encrypting all your data at rest, which can stop attackers from reading the data, even if they manage to access the backend.
Ensure that all your APIs are compatible with the mobile operating system. Implementing robust authentication can also safeguard your app from unauthorized users accessing your sensitive data and features.
While third-party libraries can be time and effort-savvy due to their pre-written code, they can also pose significant security threats. Since you didn't write the code, it might contain security flaws that attackers can exploit.
For example, Log4j's communication functionality had a security flaw that allowed attackers to inject code into the logs, a security risk that remained undetected from 2013 to 2021.
To avoid such issues with your mobile app, it's advisable to use code from trusted sources like controlled internal repositories and implement policy controls during acquisition.
With the increased adoption of smartphones and rapid digitalization, mobile apps have become a tempting target for cybercriminals. In such a situation, traditional mobile app security practices must improve. So, here are some key trends that are poised to shape these improvements in 2025.
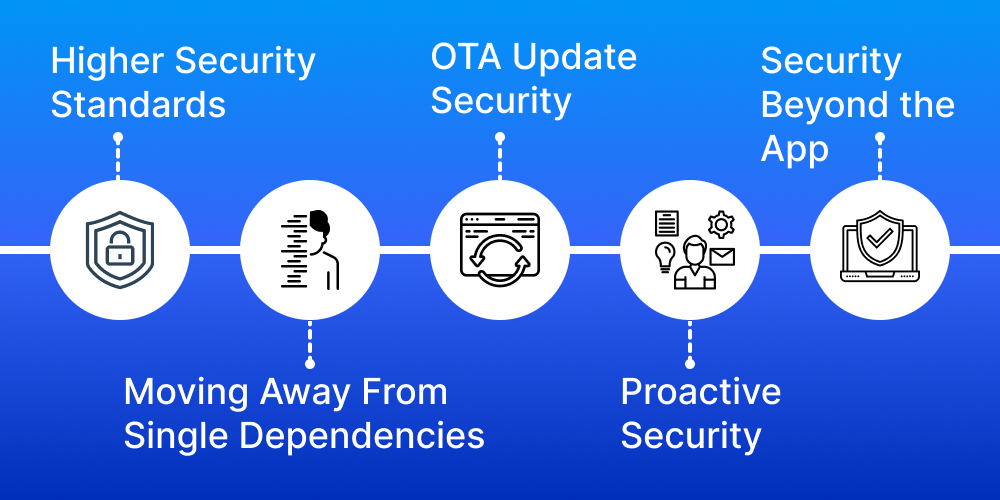
The surge in cybercrime has led to a heightened awareness among consumers and businesses about the inadequacies of current security measures. The fact that 77% of financial apps have at least one significant vulnerability demands the need for robust security. Consequently, in 2024, apps will need to adhere to stricter security standards to meet these expectations.
Companies will likely demand more comprehensive evidence of security before collaborating with or acquiring apps for their operations. Likewise, consumers are inclined to discard apps with security breaches or widely publicized vulnerabilities. These escalating requirements prompt developers to prioritize security over rapid release schedules and extensive features.
Moreover, these security standards might soon be legally mandated. With the rise in data protection regulations, developers who fail to adopt more secure practices and technologies could face hefty fines and other legal consequences.
In 2024, an increased focus on single dependencies will significantly influence the mobile app security landscape. Mobile apps, which are typically simpler and developed more rapidly than other software, often have more single points of failure. As these apps become more susceptible to attacks, developers need to shift away from this approach to reduce potential harm.
While single dependencies can expedite development, the associated risks are considerable. Even features like single sign-on, which are generally more secure than traditional login methods, can be compromised by bugs, allowing attackers to brute-force their way in. To prevent a single vulnerability from compromising the entire service, apps must incorporate multiple code and security layers.
Regular testing and extended development timelines are necessary to avoid these dependencies. Although some businesses may be reluctant to adopt these measures, they can help mitigate the damage caused by a breach, leading to long-term cost savings.
Today, mobile apps are already proactive in implementing regular security enhancements. Currently, there has been an intensified focus on these updates. The SolarWinds hacking incident has underscored the need for improved verification methods for over-the-air (OTA) updates. It prevents the delivery of harmful code to a multitude of devices through these updates.
The first step towards securing OTA updates is their encryption and authentication. By employing the most recent encryption protocols, we can thwart man-in-the-middle attacks. Additionally, cryptographic verification tools can confirm that updates originate from reliable sources before installation.
Mobile device manufacturers bear a significant portion of the responsibility for this emerging trend. These firms must incorporate technologies such as cryptography and encryption for all downloads available in their app stores and decline to host applications that are incompatible with these standards.
The increasing demand for enhanced security is prompting mobile app development companies to integrate cybersecurity measures throughout the development lifecycle rather than treating them as an afterthought.
To combat the escalating threats in the mobile landscape, developers need to prioritize security right from the project's inception. This involves embracing the principles of DevSecOps, which transform tools, cultures, and processes to position security as a collective and central obligation.
The traditional reactive stance towards security is rapidly losing its relevance as cybercrime becomes more sophisticated and the cost of data escalates. Developers are required to employ automated tools for managing vulnerabilities to comprehend their risk environment. They also need to implement necessary modifications before malefactors can exploit them.
Furthermore, penetration testing needs to be incorporated as a routine aspect of the development process rather than a concluding step applied to the finished product.
The scope of app security seems to broaden beyond the app itself. Developers aiming to adhere to stricter cybersecurity norms must understand that weaknesses in the software supply chain or development process can compromise an app's security even before its release.
The prevalence of software supply chain vulnerabilities is alarming. A study conducted in late 2022 revealed that over 75% of the apps contained AWS access tokens, thereby providing attackers with access to private AWS servers.
Trust in the software supply chain is often granted too readily and reassessed too infrequently. Constant vigilance for emerging threats, even in tools previously deemed reliable, should be a fundamental aspect of trust in mobile app security. Developers need to acknowledge the ubiquity of these risks and confirm the security of their tools both prior to and during their use.
The security of mobile apps must encompass the protection of the entire development environment. This involves using safer tools, identifying third-party vulnerabilities, enforcing higher standards on partners, and introducing restrictions that reduce potential supply chain risks.
As technology is making its way toward a more digital era, mobile app security will remain a crucial area to focus on. Although cyber-attacks have become common these days, we can still make efforts to protect the user’s information.
With the help of this blog on mobile app security, we tried our best to introduce you all to the common security threats alongside the best practices to mitigate them. Hope this information will help you prepare in advance and overcome all the potential challenges that may come in the process.
If you want to know more about mobile app security or are worried about making your mobile app secure, you can contact Mtoag Technologies anytime for expert assistance.
These are apps designed to protect your mobile device from security threats. They offer features like virus scanning, firewall protection, and secure browsing.
You can secure your apps by implementing strong authentication and encryption, regularly updating them, and using secure coding practices to prevent vulnerabilities.
To security test a mobile app for vulnerabilities, you can use tools like static and dynamic analysis, penetration testing, and checking for secure data storage.
A secure mobile app is one that protects user data, maintains privacy, and resists attacks. It follows best security practices in its design, development, and deployment.
To make an app secure, use secure coding practices, implement strong encryption and authentication, conduct regular security audits, and keep the app updated.